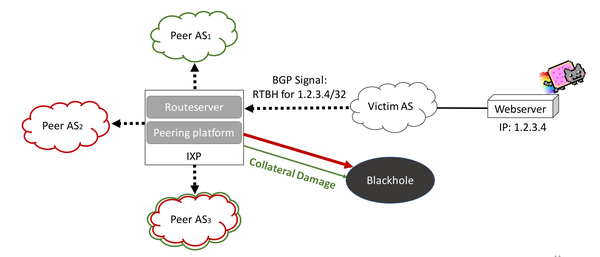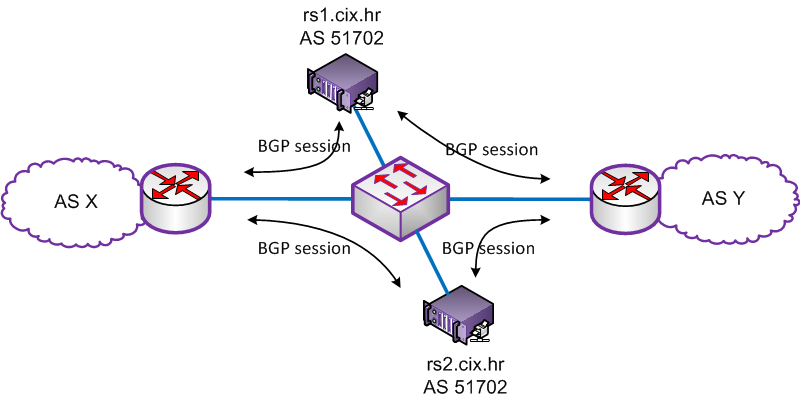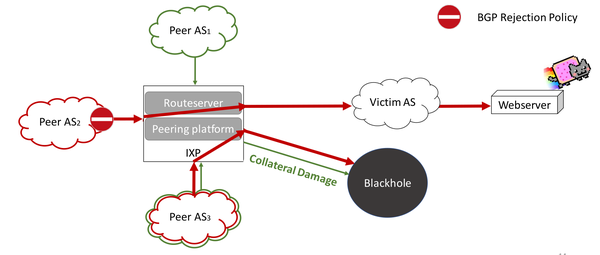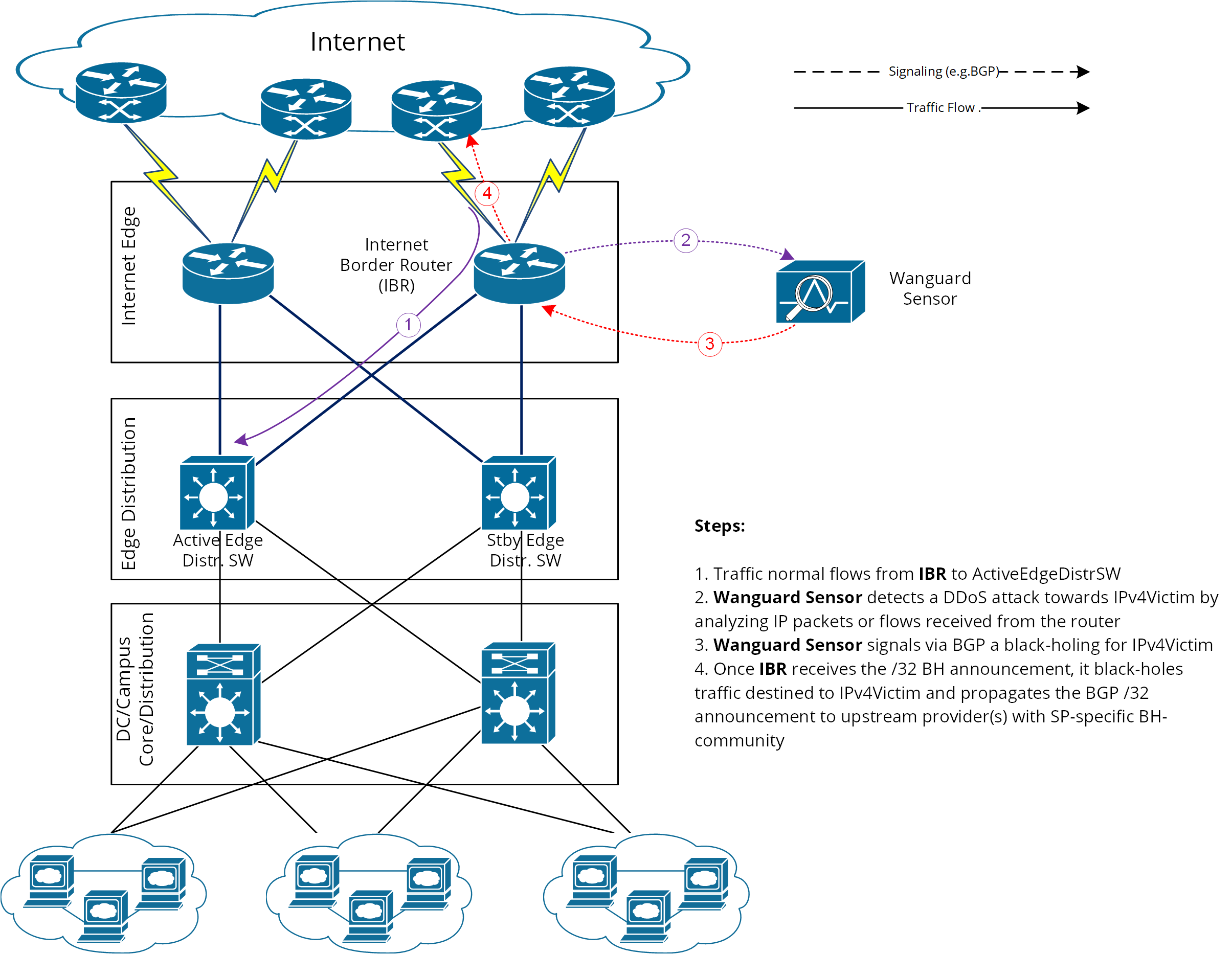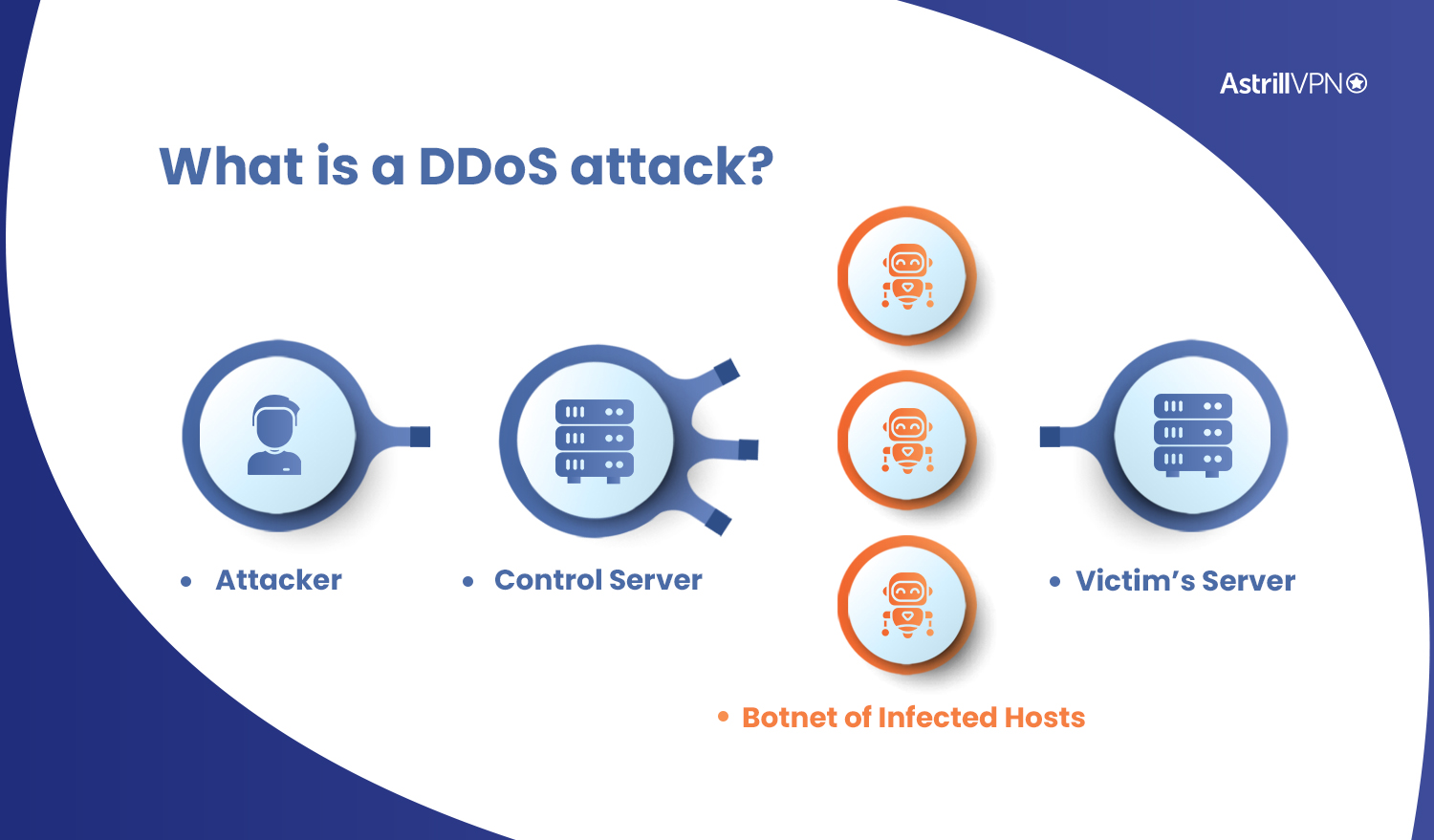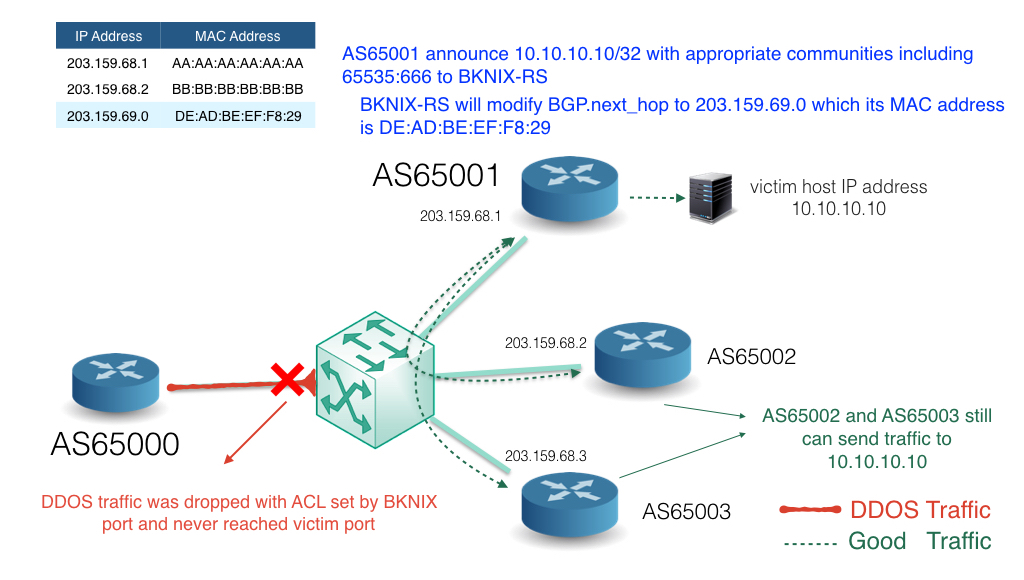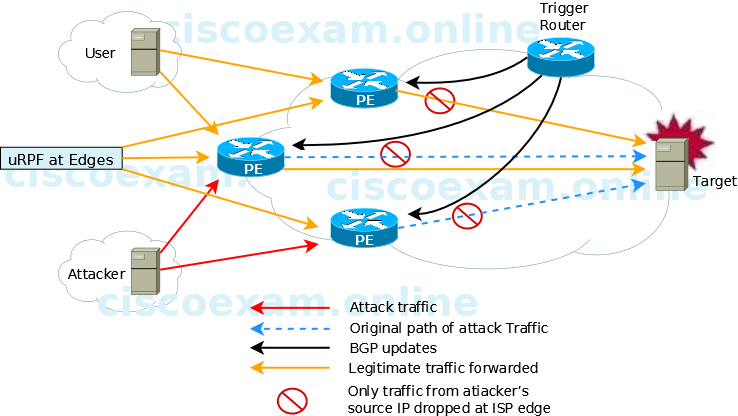
When implementing source-based remote-triggered black hole filtering, which two configurations are required on the edge routers that are not the signaling router?

How to configure Remotely Triggered Black Hole routing to protect from DDOS attacks (with bonus) - RouterFreak